Enroll Windows device automatically using Group Policy
In this series of learning different enrollment methods, till now we have seen mainly how user can enroll their device manually that leverage BYOD (If you haven’t heard of BYOD yet, refer here). In this post, we will learn how we can enroll windows 10 or 11 devices using group policy. Using Group policy, we can automate the device’s enrollment to Intune. This approach is basically used for bulk enrollment of AD joined devices. With this, enrollment process starts in the background once you sign in to the device with your Azure AD account.
What’s the need ?
It is not possible to enroll thousands of windows devices in a GO using manual process which requires manual intervention. Here comes the need of some automated way like GPO, use of DEM account, corporate, Autopilot, Bulk enroll, Co-management.
Prerequistes
- AD joined Windows 10 >= version 1709
- MDM configuration and Intune settings
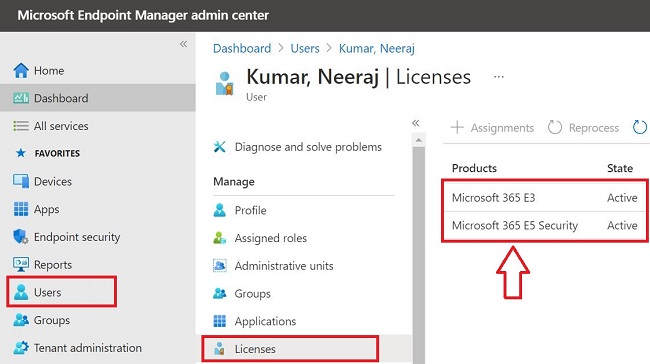
A. Verify License (EMS + E3, EMS + E5, Microsoft 365 E3, Microsoft 365 E5 etc)
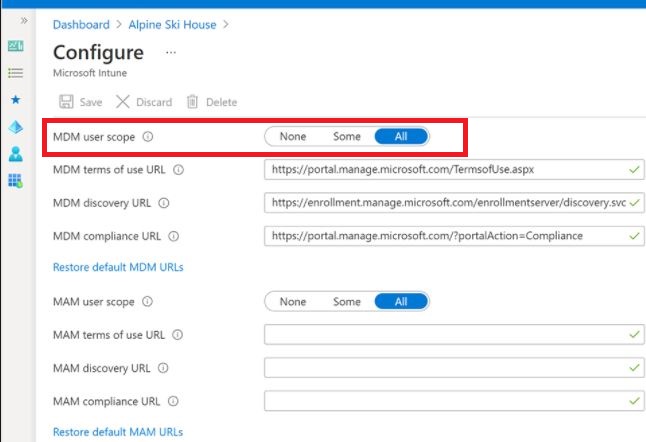
B. Verify auto-enrollment is activated
C. Verify enrollment restriction
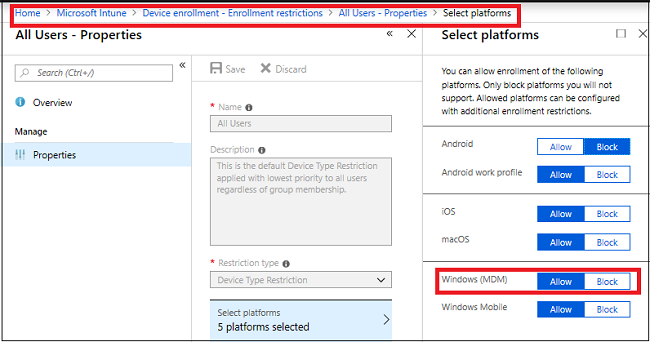
- Verify that Azure AD allows the logon user to enroll devices.
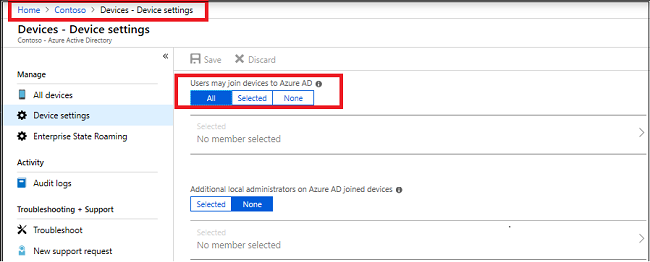
- Devices should be hybrid Azure AD joined
The target device should be hybrid Azure AD joined which basically means device must be joined to both AD and Azure AD. To cross check the device is hybrid Azure AD joined or not, run below cmdlet on the device
dsregcmd /status
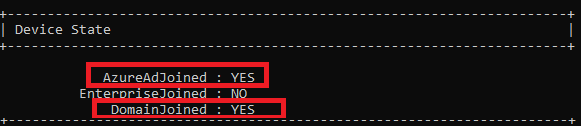
Note: The device is properly hybrid-joined if both AzureAdJoined and DomainJoined are set to YES
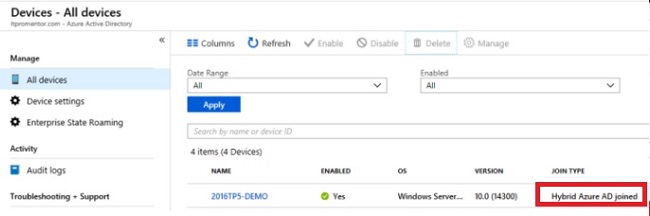
We can even check from Azure AD under devices section like below -
Configure auto-enrollment group policy
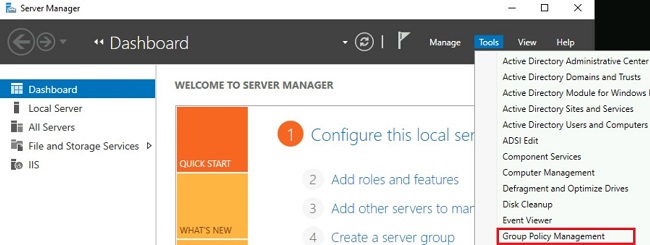
Step 1: Open Group Policy Management from the start menu. Alternatively, type gpmc.msc in Run window.
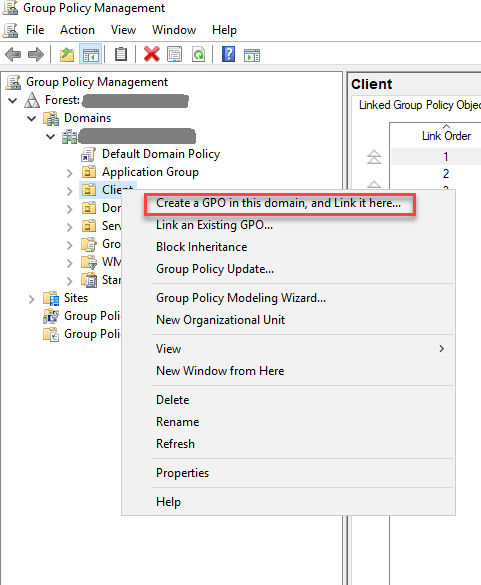
Step 2: Select OU where you want to apply GPO, right click and select Create a GPO in this domain, and Link it here as shown below -
Step 3: Give it a name such as Intune Auto-enrollment and edit the Group Policy.
Now, under Group Policy Management Editor, navigate to Computer configuration > Policies > Administrative Templates > Windows Components > MDM.
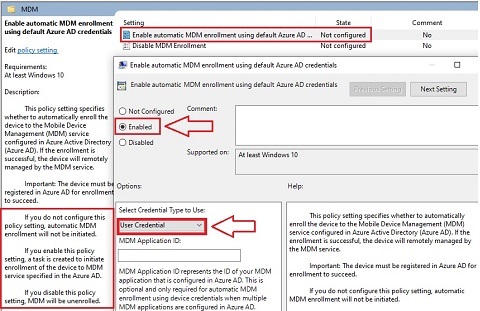
Step 4: Double click Enable Automatic MDM Enrollment Using Default Azure AD Credentials
- Select Enable
- Select User Credentials in Credential type.
For a single user, its straight forward refer here
What happens in backend
This policy createa a task in task scheduler which will try to auto-enroll the device in every 5 minutes. To view this, open Task Scheduler, navigate to Task Scheduler Library > Microsoft > Windows > EnterpriseMgmt. A task schedule with the name Schedule created by enrollment client for automatically enrolling in MDM from AAD should present here.
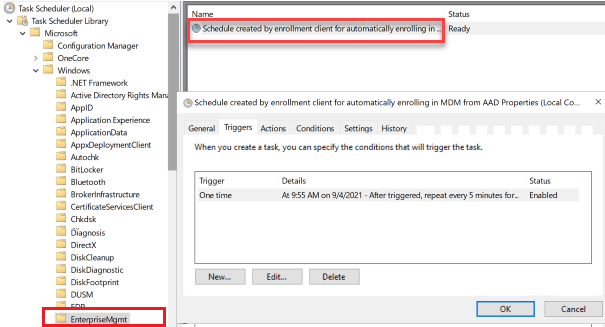
This task executes following command which helps in auto-enrollment:
%windir%\system32\deviceenroller.exe /c /AutoEnrollMDM
Verify successful enrollment
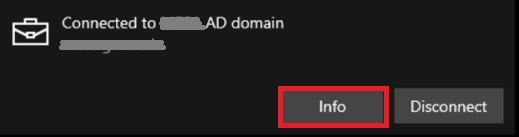
Step 1: Go to Settings > Accounts > Access work or school.
Step 2: Click Connected to Azure AD domain then click Info.
Troubleshooting Guide
If you see Info button is missing, enrollment might have failed. To find the root cause, login to the device with corporate account(Azure AD cred). Run gpupdate /force. Now, sforementioned task scheduler will kick for enrolling the device to Intune.
The enrollment progress/process can be checked through event viewer, launch event viewer (eventvwr.msc) and navigate to Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider and select Admin.
Event ID 75 means success.
Event ID 76 means failure.
For detailed Microsoft article, please refer here for more details.